Passwords –
What's Cracking?
The
purpose of this report is to demonstrate different password cracking techniques
and software.
This report was written for the Penetration Testing course taught by Tero
Karvinen.
-------------------------------------
Installing Hashcat and wordlists/hashes on
Windows
Installing Hashcat on windows was extremely quick and enjoyable, I
navigated to the official hashcat
website
and downloaded they binaries that came compressed in a .7z format. I made a directory
on my desktop
and extracted the folder inside the compressed archive file. Then, I downloaded
a compressed archive hashfile called
OPNorthKorea (MD5) and ABC (SHA1) from adeptus.mechanicus.com
(the WH40K reference is appreciated) and extracted them into my workspace.
Lastly I needed a wordlist to use against these hashes. I decided to download
the classic rockyou.txt, which contains over
14 million words from naïve-hashcat github
(be wary, this is a download link). This can be done through curl as well:
![]()
Now we're ready to benchmark and crack on Windows!
-------------------------------------
Benchmarking Hashcat
Hashcat has a famous capability to crack
passwords by using the users GPU, but how does it compare to CPU?
For this test I ran hashcat on my Windows 10 machine, with my Radeon
RX 480 GPU, and since hashcat didn't
want to cooperate with me in benchmarking the my AMD
FX-8350 Eight-Core Processor, I had to run the CPU
test on my Kali Linux virtual machine.
I ran the test by running the following commands on my machines:
·
(Win
10) ./hashcat64.exe -b
·
(Kali Linux) hashcat -b
(The -b
flag stands for benchmark)
Windows 10 (GPU):
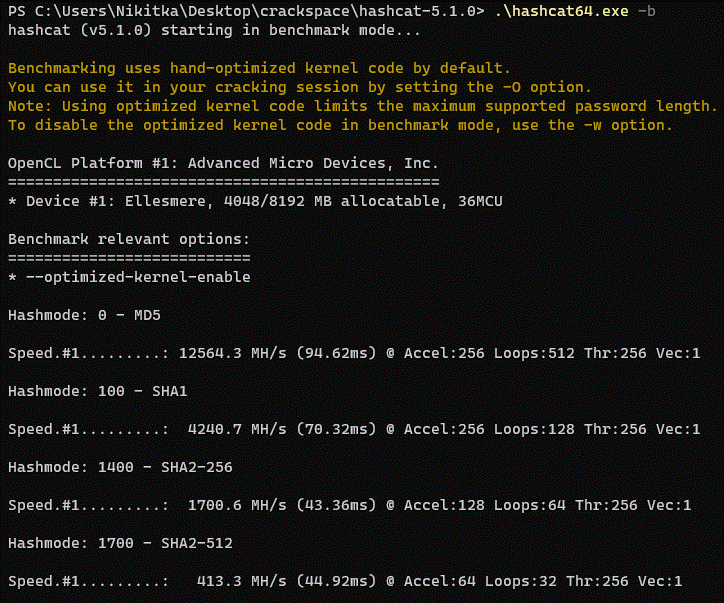
Kali Linux
(CPU):
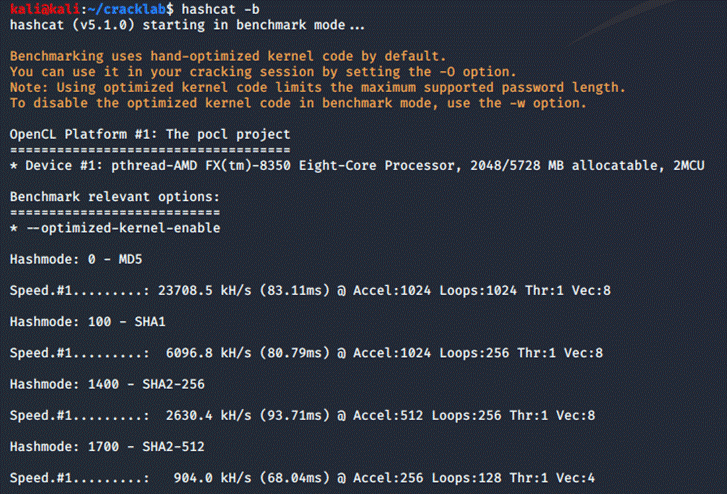
The values
we should be looking at are the xH/s, meaning hashes per second, kH/s meaning
thousands of hashes per second,
MH/s meaning millions of hashes per second. I unfortunately couldn't find any
concrete evidence for this, except for forum
posts.
Through
this benchmark, we can by example deduct that through GPU, hashcat cracks
approximately 12 564 300 000 md5 hashes
per second, while by using my CPU, it cracks "only"
23 708 500 MD5 hashes per second. I believe that by running this
benchmark
partly on a virtual machine I distort the results. But by looking at the
results, I don't think it matters that much, since my GPU
outperforms my CPU by thousands of times.
-------------------------------------
Cracking using hashcat and GPU
Now that
benchmarking is out of the way, let's get cracking!
Although hashcat has a complicated syntax at first glance, by using a cheatsheet and the
official documentation,
password cracking turned out to be quite easy.
The OpNorthKorea list is encoded in MD5:
And in order for hashcat to crack it, we need to specify the -m (hash type)
And by looking at the documentation we need to use the -m 0 flag:
![]()
The syntax
I used is:
./hashcat64.exe (hashcat) --force -a 0
-m 0 -o ../result.txt ..\OpNKorea-md5.hash ..\rockyou.txt
The flags: --force => ignore warnings, -a 0 => attack mode 0 (straight
mode, which is a dictionary attack),
-m 0 => hash type (the list can be found here)
-o => outputfile after which we need to specify the hashfile and the
wordlist to use for the attack.
But on my first launch I ran into a problem:
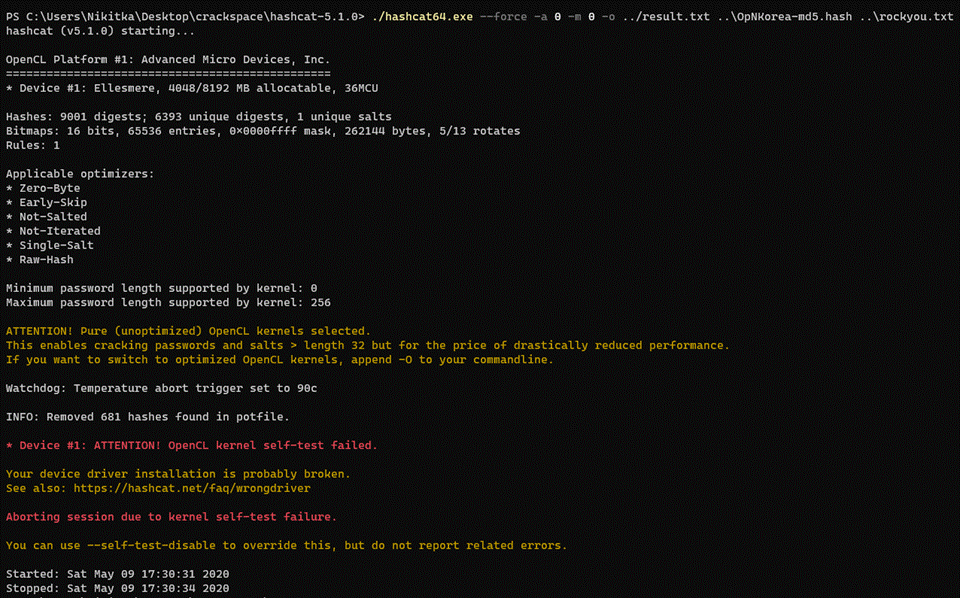
But by adding the --self-test-disable flag the cracking starts just fine:
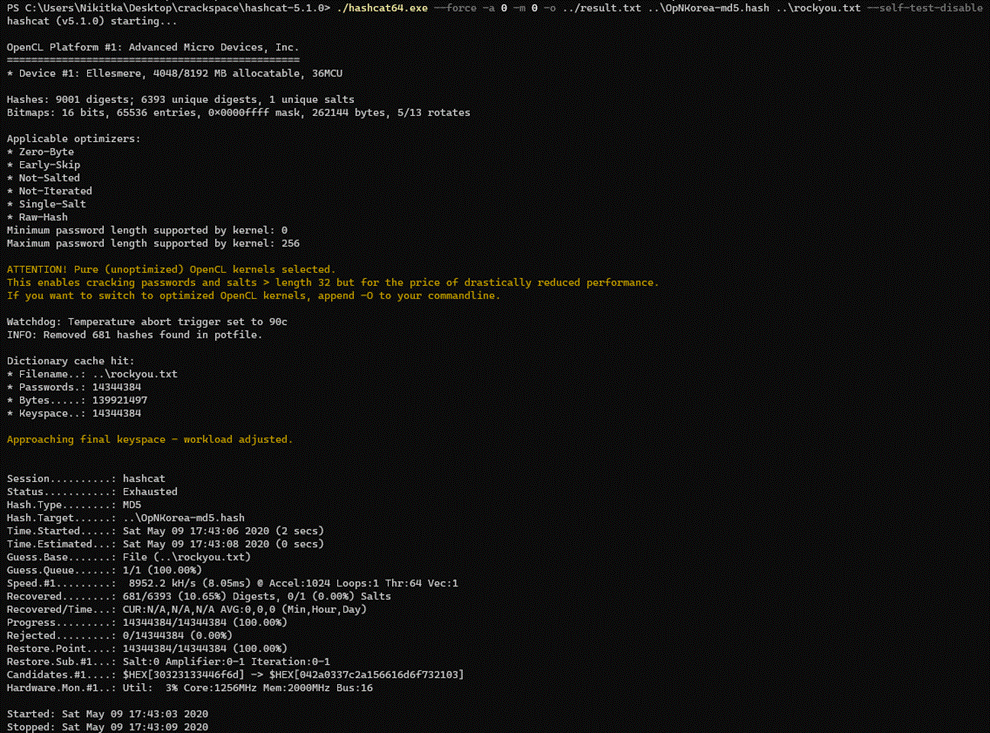
The OpNorthKorea hashfile had over 9000 (9001 to be
precise) hashes, out of which hashcat managed crack 681 in the span of 6
seconds:
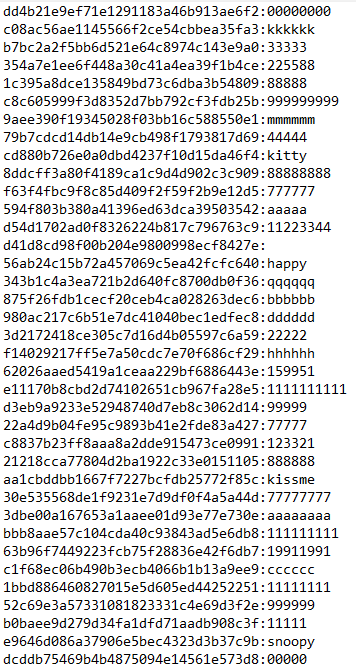
A piece of the output file, displaying the cracked
hashes.
Next up, I wanted to see the SHA-1 cracking
capabilities of hashcat.
For this, I only needed to change the hash filename and the hash type according
to the hashcat documentation, since I
didn't find a need to keep the previous output file I decided to overwrite it:
![]()
./hashcat64.exe --force -a 0 -m 100 -o
../result.txt ..\abc-sha1.hash ..\rockyou.txt --self-test-disable
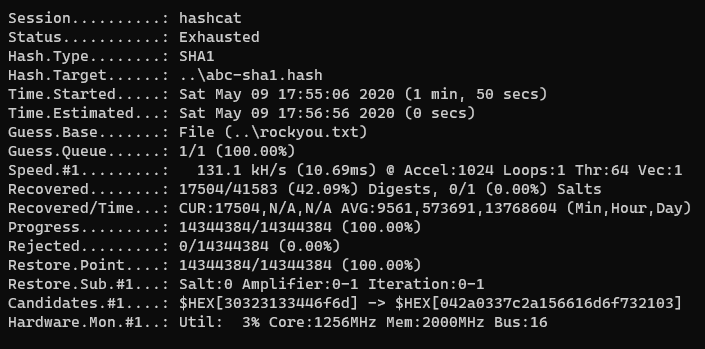
This time around, the hash file had over 49 thousand
hashes, so the cracking took much longer, especially if we look at our
benchmarking
results, the time for SHA-1 hash cracking was about three times slower than for
MD5.
And by looking at the Recovered parameter in the results, we can see that we
got almost half of the hashes cracked.
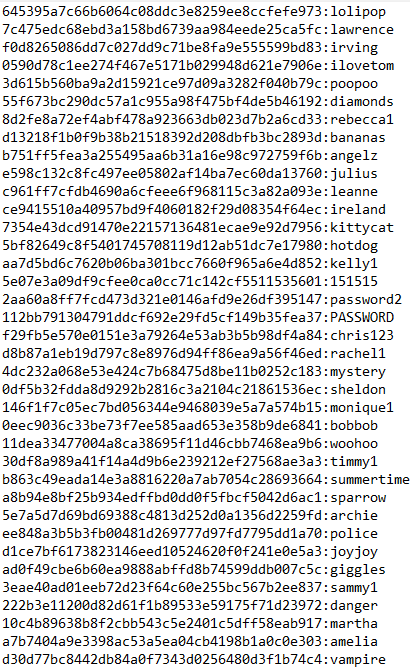
A part of the output
In the end, I found hashcat to be quite enjoyable and
quick, although I found the syntax a little bit scary at first.
-------------------------------------
Cracking SSH Private
Keys with John The Ripper
John and all of the utilities used in this section are
pre-installed on Kali Linux.
When generating an SSH keypair, the user creating them has an option to enter a
passphrase, but with a correct wordlist,
John can crack the private key passphrase, granted the attacker has a correct
wordlist.
The prerequisites for this lab were as follows:
I connected my Xubuntu 18.04 and Kali to a Host-Only
adapter on Virtualbox (For more details on how to do it, refer to my Metasploit report).
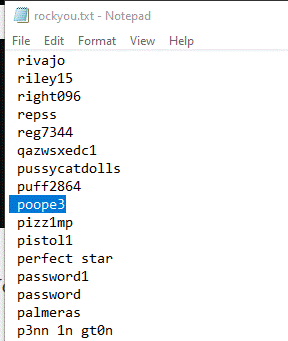
Then, I used a password (poope3) from rockyou.txt as a passphrase for the
private key:
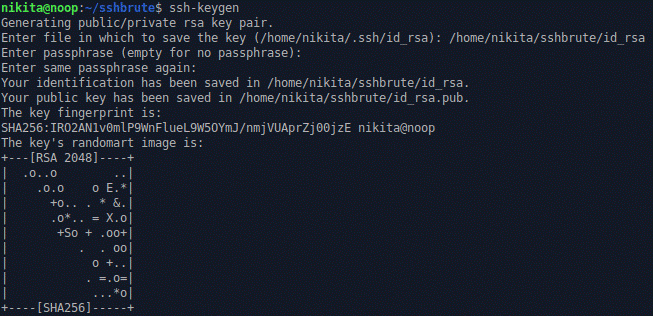
Then, in order to simulate perhaps the most insecure
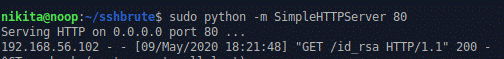
server of all time, I hosted the private key using Python's
SimpleHTTPServer
and downloaded it onto my attacker machine using wget:

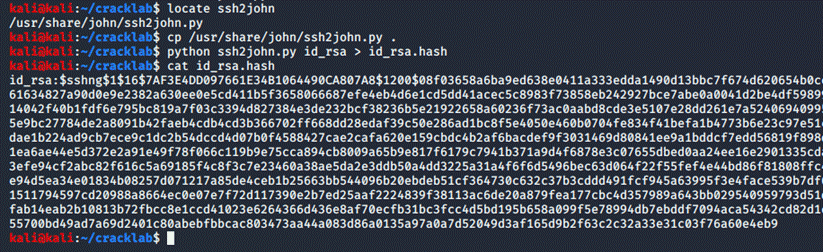
Then, I used ssh2john.py in order to convert the
id_rsa file into a format john the ripper accepts:
Now that all of this is in order, we can crack the
hash with john, which has a self-explanatory syntax:
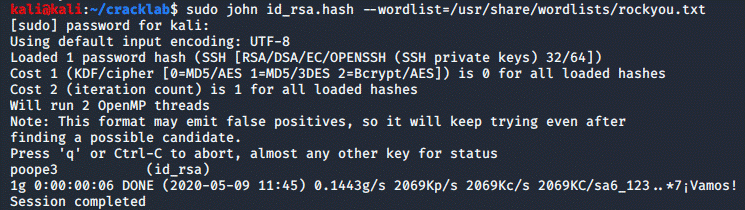
And just like that, we converted an ssh private-key
and cracked it's passphrase!
Next up, we'll do some HTML/HTTP brute-forcing.
-------------------------------------
Setting up the
environment
In order to do some brute-forcing in HTML/HTTP I
decided to write my own environment using Python and the Flask framework by heavily relying
on these tutorials: Part
1 & Part
2
But Kali does not have pip natively in order to install , and pip for python
2.7 is no longer available through apt, but thankfully we can install pip
for python3 by running: sudo apt install
python3-pip
After which we can run:
pip install Flask
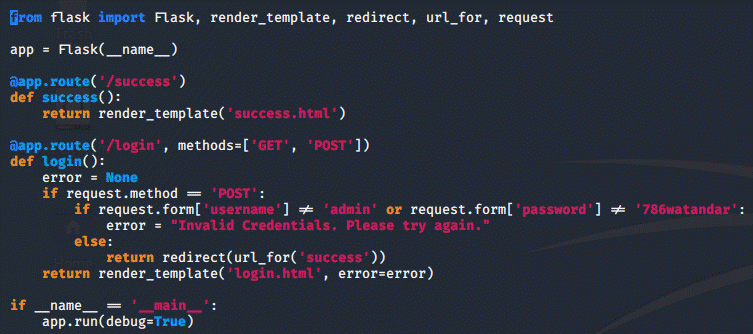
My end results ended up looking like this:
app.py, I set username as admin for convenience and randomly selected a
password from rockyou.txt:
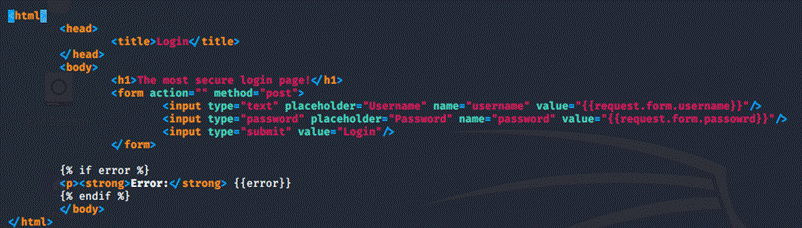
login.html:
success.html:
Now that the environment is set up, we can run
python3 app.py
And Flask will do the rest:
-------------------------------------
Cracking HTTP
Now that the webservice is set up, we can start cracking it.
For that, I'll demonstrate how you can do that with both wfuzz
and hydra
(which are both native to Kali):
=-=-=-=-=-=-=-=-=-=
Hydra
In order to
brute force our website, let's pretend we don't know the source code to it.
First, we'll need to find out what type of parameters and what the error
message is.
For that we'll use Burp Suite and foxyproxy.
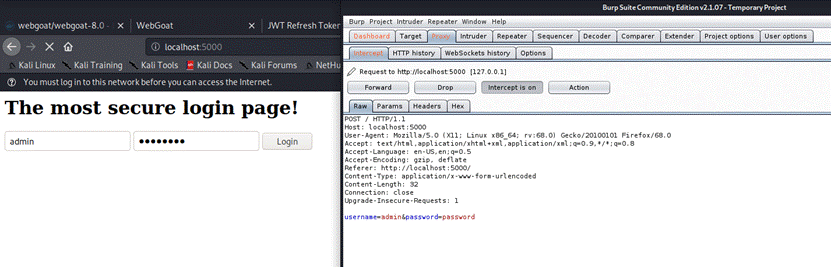
After
configuring foxyproxy to work with Burp Suite, we open Burp Suite, go to
the proxy tab and make sure "Intercept" is set to "On",
then we submit wrong credentials to see how the post request looks like:
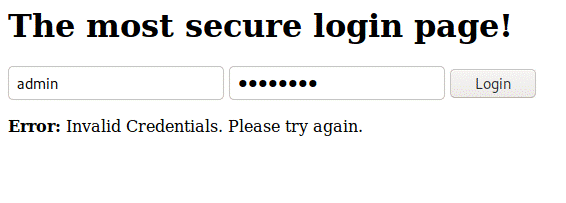
We also need
the error message, so we click on "Forward" in Burp Suite, and see
the following error message on the site:
Now, we have
all the parameters we need we can enter run the tool:
hydra -l admin
-P wordlist 127.0.0.1 -s 5000 http-post-form "/:username=^USER^&password=^PASS^:Invalid
Credentials. Please try again." -V
Syntax: -l => single username, -P => password list, <ip
address>, -s => port number (intuitive, right?), http-post-form => the
HTTP form we are using,
the last part is tricky in quotes, we first have the path we are attacking
"/" then the next parameters, which are the username and password we
are brute-
forcing are separated by a colon ":" and input the way they were in
burp, except the parts we are "bruting" are incicated with ^USER^ and
^PASS^, then we
separate the error message with another colon.
(NOTE: The -I flag was used by me in order to ignore a warning from
a session is interrupted)
UPDATE: Forgot to mention the -V flag => verbose mode.
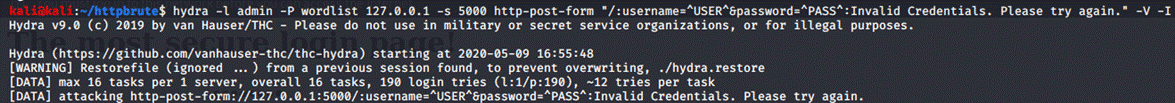
After letting the tool run for a couple of seconds, we are hit with a match:
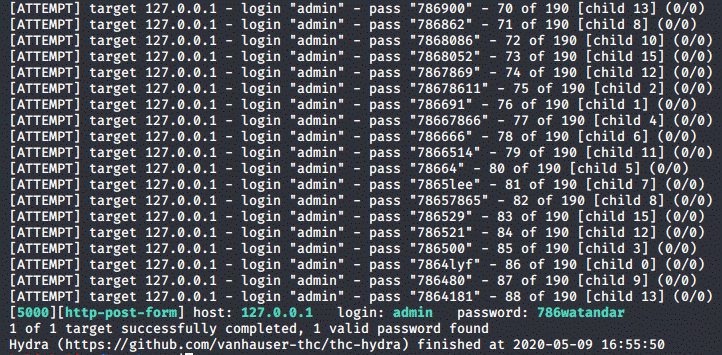
And that's it! We have the credentials in order to get in.
Now, I'm not really a fan of Hydra's syntax, so let's check out Wfuzz.
=-=-=-=-=-=-=-=-=-=
Wfuzz
First, in order to make this easier on my back end I
piped 190 strings which contained the real password
from rockyou.txt into another file I named "wordlist".
Then, I used a slightly modified version of the "Fuzzing POST
Requests" syntax of the documentation:
wfuzz -w wordlist -d
"username=admin&password=FUZZ" http://localhost:5000/
Flags: -w => wordlist path, -d => POST request data
And by looking at the responses, we can see that the
correct response returns a HTTP code 302, meaning that this request
got us redirected to the "success" page:
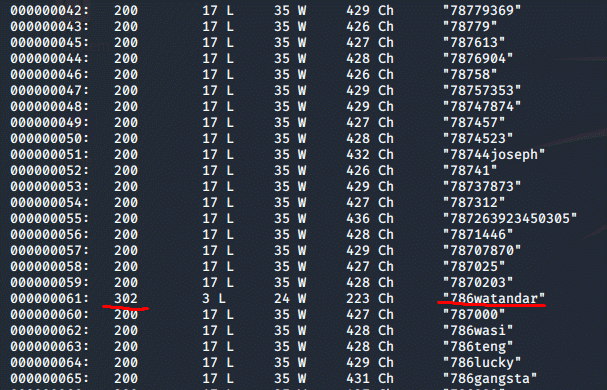
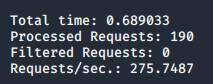
The time it took for the fuzzing
And that's pretty much it, the attacker can use this password to log in,
and if one know what type of response they're looking for,
it's quite easy for them to filter through them with the --hc flag as well,
which means "hide responses with the specific code".
-------------------------------------
This concludes my report of brute-forcing, I hope you
enjoyed reading it as much as I enjoyed working on it.
Return to Main Page