Web Fuzzing –
ffuf
The purpose of this report is to demonstrate
the different usages of ffuf web fuzzer
on a custom python
back end for a Penetration Testing course taught by Tero
Karvinen during Spring 2020.
ffuf is an open-source web fuzzing tool written
in go that was first made publicly available in 2018.
It has already made itself quite a reputation in the pentesting communities due
to its speed and ease-of-use
- and many hackers have already started using it instead of tools like wfuzz for parameter, directory or
subdomain fuzzing.
-------------------------------------
Babby's First
Vulnerable App
For this demonstration I wrote my own although very simple vulnerable
back end using Python's Flask
framework.
The back end is a modified version of the one I used for my report on password cracking.
The current source code is available to be looked at – at the end of this
report.
=-=-=-=-=-=-=-=-=-=
Let's get to it
First, I started my app by running the command
python3 app.py
And navigated to the webpage with the url http://localhost:5000/
Now, let's try to see what else is hidden on
this webapp besides the login page by using fuff and the command:
./ffuf
-w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u
http://localhost:5000/FUZZ
Flags: -w => wordlist, -u => URL/host
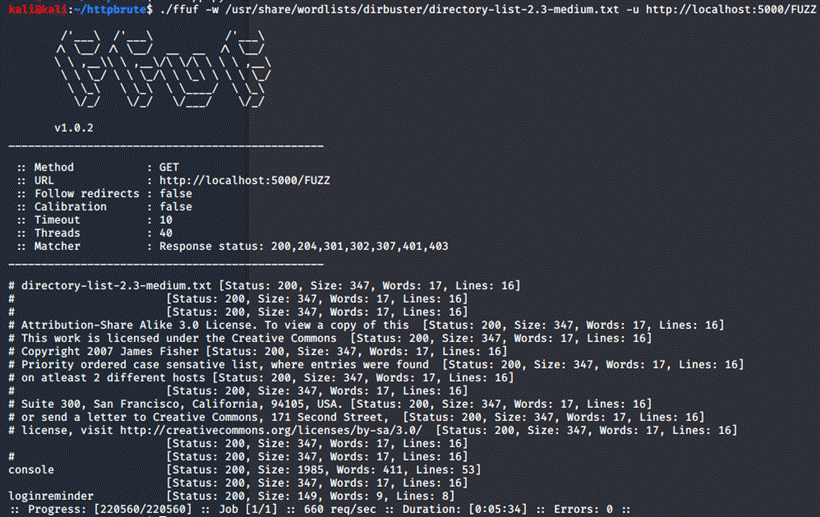
Now there's multiple things we found: The
whitespaces and the hashtag lead back to the login page,
while "console" is the Flask debug console that need's the PIN from
the launch to access, but there's one thing that seems interesting,
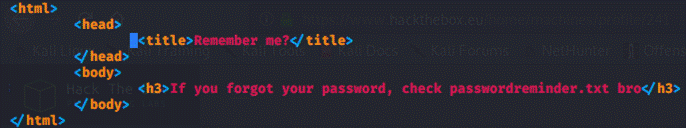
"loginreminder", let's check it out!
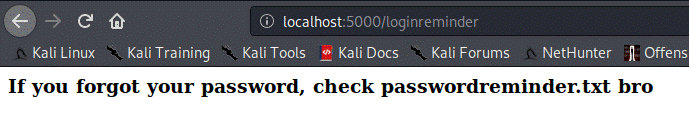
Interesting, but there's no endpoint name
/passwordreminder.txt or /passwordreminder:
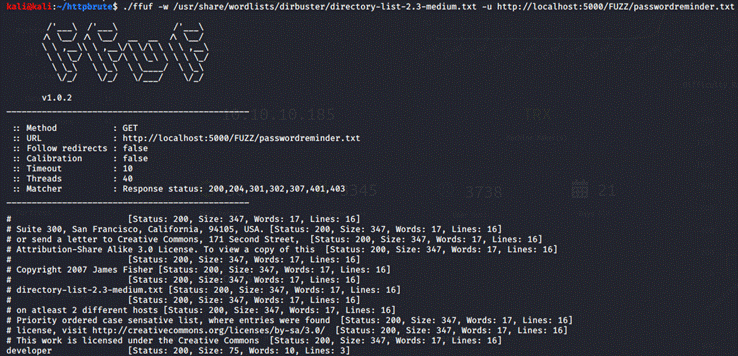
But we can check if there's a file like that in
some other folder by running the same command as last time, but for the URL,
we add /passwordreminder.txt in the end:
And now that we know where that file is
located, let's check it out:
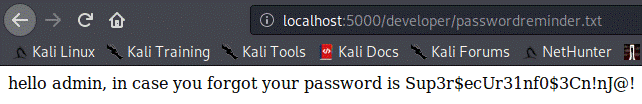
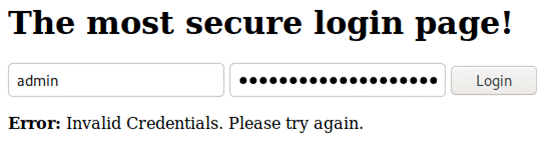
Hooray! Now that we got the password, let's try to log in with admin:Sup3r$ecUr31nf0$3Cn!nJ@!
But there's a problem, admin doesn't seem to be the correct username:
Let's try to get a hold of the type of request
being sent to the server using a proxy and fuzz the parameters.
For this, let's use Burp Suite and
send a login request:
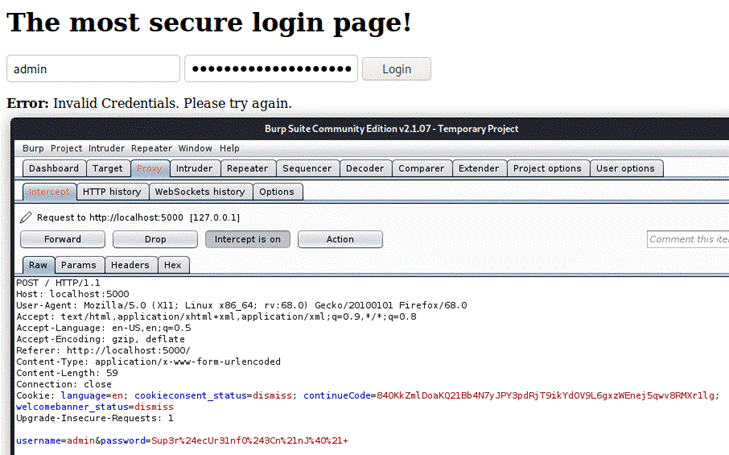
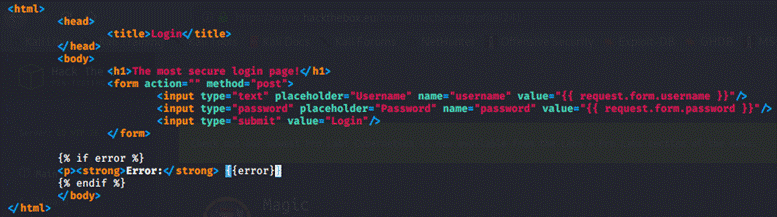
Looks simple enough, we just make a POST request
and use the parameters username=username&password=password:
./ffuf -w
/usr/share/wordlists/fern-wifi/common.txt -X POST -d
'username=FUZZ&password=Sup3r$ecUr31nf0$3Cn!nJ@!'
-u http://localhost:5000/
Flags: -w => wordlist, -X => type of request send, -d => POST data, -u
=> URL/host
NOTE: When dealing with data that contains '$', make sure to include it in
single quotes (') instead of "regular" quotes ("),
or else bash is going to think the dollar signs are events or commands.
But we ran into a problem, we didn't get any results:
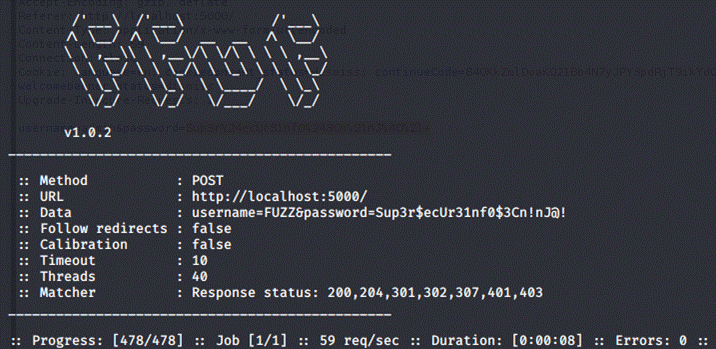
In this case, it's due to ffuf not sending the data with a correct
Content-Type:
=-=-=-=-=-=-=-=-=-=
PROOF OF
CONCEPT:
If we run this command through a proxy, aka
Burp Suite by adding the -x flag, along with the address for
your proxy
(which in my case is http://localhost:8080),
we can what's happening behind the scenes:
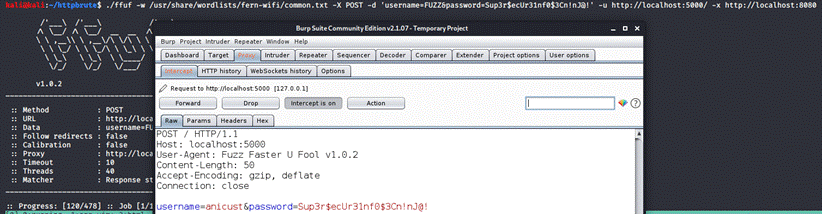
And from these results, we can see that ffuf
didn't set the Content-Type for this request, but there is a workaround.
=-=-=-=-=-=-=-=-=-=
Now if we add yet another flag, which is -H – which
stands for Header, we can set it to the correct content-type, which is
application/x-www-form-urlencoded:
./ffuf
-w /usr/share/wordlists/fern-wifi/common.txt -X POST -d
'username=FUZZ&password=Sup3r$ecUr31nf0$3Cn!nJ@!'
-H 'Content-Type: application/x-www-form-urlencoded -u http://localhost:5000/
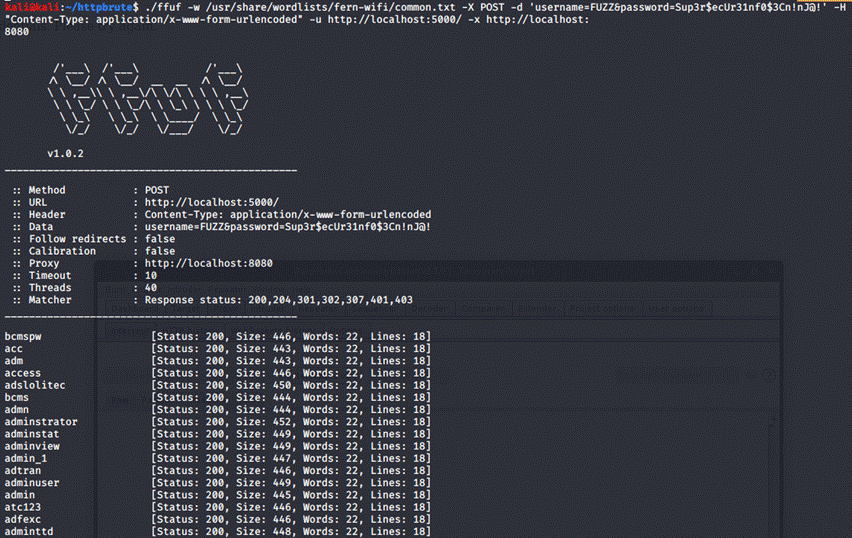
Now that's a lot of
responses! But only one of is the correct one, can you spot it?
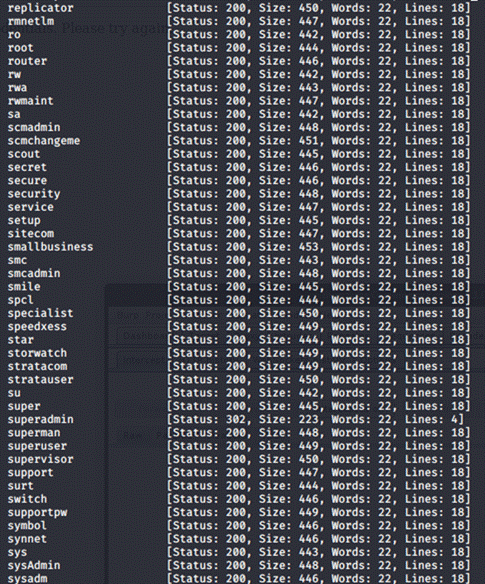
That's right, the correct username is
"superadmin", so let's log in with the creds superadmin:Sup3r$ecUr31nf0$3Cn!nJ@!
![]()
And there we have it. We have fuzzed through
the application and got the login.

-------------------------------------
Could I Have
Some Sauce With That?
The little back end for this project, although
far from perfect was fun to write, as stated before, I used the Flask framework
for Python to make the back end, and the rest was made with Python:
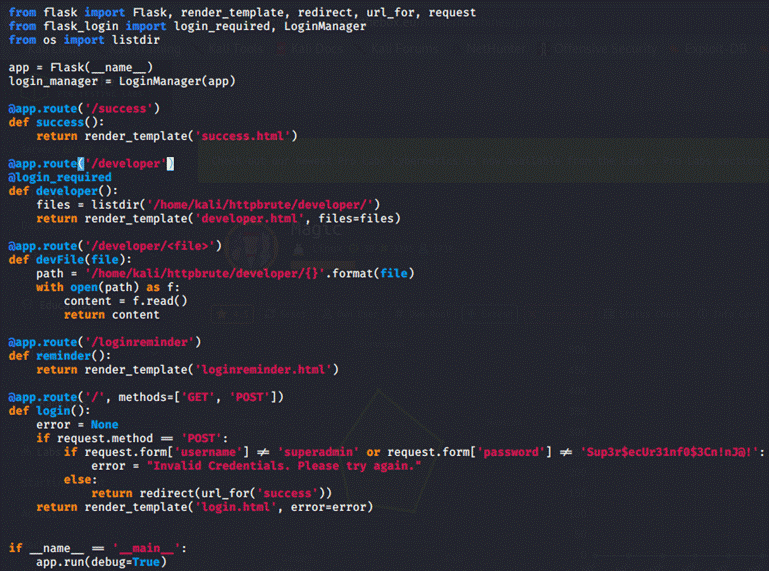
app.py:
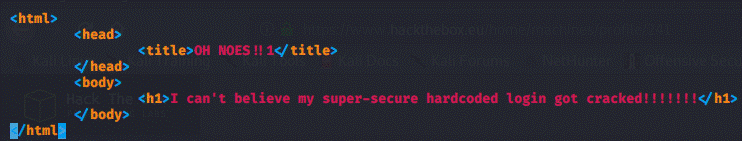
success.html:
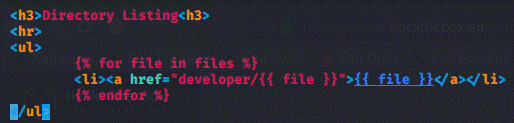
developer.html (although it was not displayed
in this report, due to it not being supposed to be seen):
loginreminder.html:
login.html:
-------------------------------------
This concludes my report on web fuzzing with
ffuf, I hope you enjoyed reading it.